The following is a closer look at one of the most active Pro-Russian ‘hacktivist’ groups currently operating during the Ukraine-Russia war, called KillNet.
There is a lot of conjecture around the group and this report is not intended to answer any questions about their abilities or skills, that can be studied by people far more knowledgeable and skilled than myself. This is instead a report to provide situational awareness and highlight the possible organizational structure of the group.
This is a work in progress and any corrections are welcome, I guess that KillNet will see this report as they have mentioned me in their chats before. If you would like to correct anything added here let me know.
I am aware that it has been reported that KillNet has been doxxed, however I will not be speculating or including that in this report, again others can explore that information.
KillNet declaration of War:
KillNet appears to have started operating as a hacktivist group on 25 February 2022. Prior to this KillNet appeared to have been selling a cyber tool. KillNet first appeared on Telegram, but as far as I have seen they also have a small presence on Twitter.
25 February: KillNet officially declares war on Anonymous,a direct result of several Anonymous factions declaring they are in ‘Cyberwar’ with Russia.
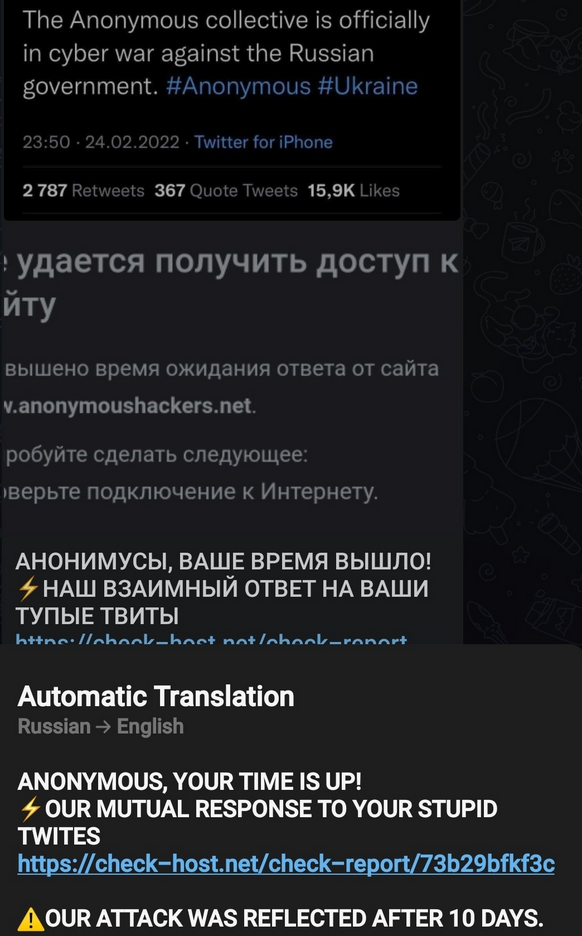
KillNet from this point gets busy, not only conducting DDoS attacks, but also creating a semi-formal organization that appears to have a sizable force. Their Telegram pages have well over 70,000 members.
The following is a timeline of KillNet organization and preparation in the war up until today.

KillNet Order of Battle (ORBAT):
It appears from reviewing KillNet telegram channels that they have created a semi-formal structured organization. With different levels of superiority, command lines and tasking. This does suggest that regardless of their sophistication levels, they have a sound level of command and control structure. Below is an ORBAT I was able to create after review of KillNet Telegram pages.

All of these groups have reportedly been active in attacks against numerous countries. It is unclear how autonomous the ‘Special forces squads’ are, but they appear to take tasking from both KillNet and Legion. It also appears that Legion has the autonomy to act on their own without centralized orders from KillNet.
KillNet mentioning that Legion acted on their own in regard to the alleged attempted attack on Euro-vision.
KillNet also has what appears to be its own media and information department, the Telegram page, Cyberwar. It echos posts from KillNet and Legion and provides additional information. It appears threat KillNet has a well-developed ORBAT that suggests some level of operational knowledge.
Documented KillNet attacks:
I won’t cover off on all KillNet attacks, just several which have made the most impact.
29 March: Bradley International Airport in the United States confirmed they were impacted be a DDoS attack after Killnet declared they had attacked them. https://www.newsweek.com/us-airport-hit-cyberattack-over-ukraine-no-one-afraid-you-1692903
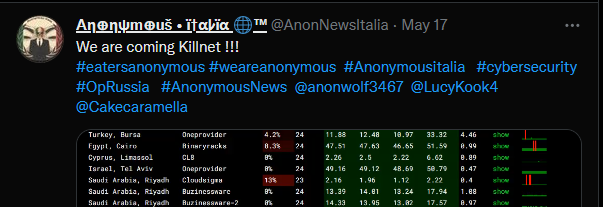
April: KillNet took control of an anonymous faction Twitter account: AnonNewsItalia for several days. The account shared pro-KillNet posts for a period before the original owners fixed the issue. https://mobile.twitter.com/AnonNewsItalia
As you would guess AnonNewsItalia is out for revenge and has been leading the charge in doxxing and exposing KillNet infrastructure.
Some observations about KillNet. I can not speak to their technical skill or sophistication other than that they have had some impact against several countries. What Is with noting is that KillNet:
· KillNet has a decent organizational structure, suggesting they must have a moderate force to deploy attacks and conduct campaigns.
· KillNet must spend some effort on reconnaissance and mission planning that suit their abilities, all politically motivated. There mission is to impact foreign countries to try and influence their actions against Russia.
· Regardless of their level of sophistication they are still be motivated, have high intent and have the opportunity to conduct cyber-attacks across Europe and the United States which makes them a threat.
As I mentioned at the start of this report I will leave the technical analysis of KillNet capabilities and sophistication to others far more skilled than myself. I recommend checking out https://twitter.com/UK_Daniel_Card for real-time updates as he has started to look at KillNet and has a report available here: https://www.pwndefend.com/2022/05/18/killnet-area-they-really-a-threat/
Follow my Twitter for real-time updates of KillNet and other cyber related events from the Ukraine-Russia war. https://twitter.com/Cyberknow20
